Android Studio provides you the option to inspect the network traffic of your own app in the Profile tab. There might be situations where you would like to see what API calls are being made from a production app. For example, when reviewing/testing current and old production builds of an app or doing a security review of an app (e.g. sideloading APKs).
In those cases it can be handy to have a specially prepared Android Virtual Device (AVD) ready to see what an app might be doing.
This guide will explain how to setup a specially prepared AVD that you can use to monitor any network traffic of any app installed in the emulator even when it’s communicating over a secure connection (HTTPS). Since this method does not work with the “Google Play Enabled” AVDs provided in Android Studio, I’ll show you a workaround for this as well since many apps do rely on functionality from the Google Play Services framework.
Installing mitmproxy
To inspect the network traffic, we will be using mitmproxy (this guide will use mitmweb a web interface so that you can use your browser to inspect the traffic). As the name indicates, it is able to view the network traffic by adding itself as a proxy between the app and the (api) server.
Depending on your OS, you should follow this install guide: https://docs.mitmproxy.org/stable/overview-installation/
Since I’m on a Mac, I used brew to install it. The rest of the guide will assume you’re on a Mac but you should be able to adapt to any changes required for your platform.
Creating the AVD
-
Click “Create Virtual Device”
-
Select a non play store device. I will use a Pixel 3 XL for this example
-
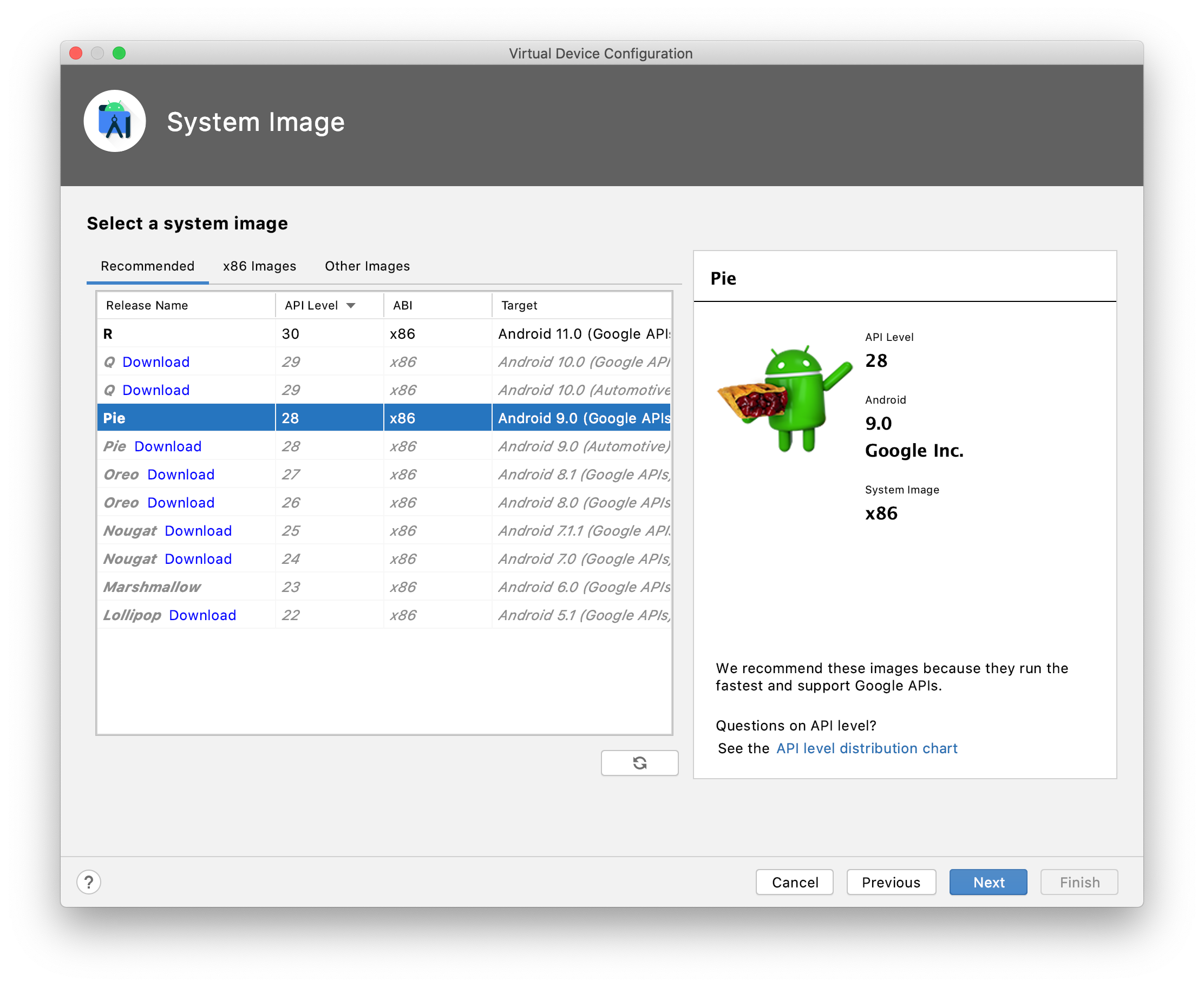
Select a system image. From my experience API level 28 and ABI x86 (Android 9.0) works best. Newer API levels might prevent you from uploading your custom (CA) certificates.
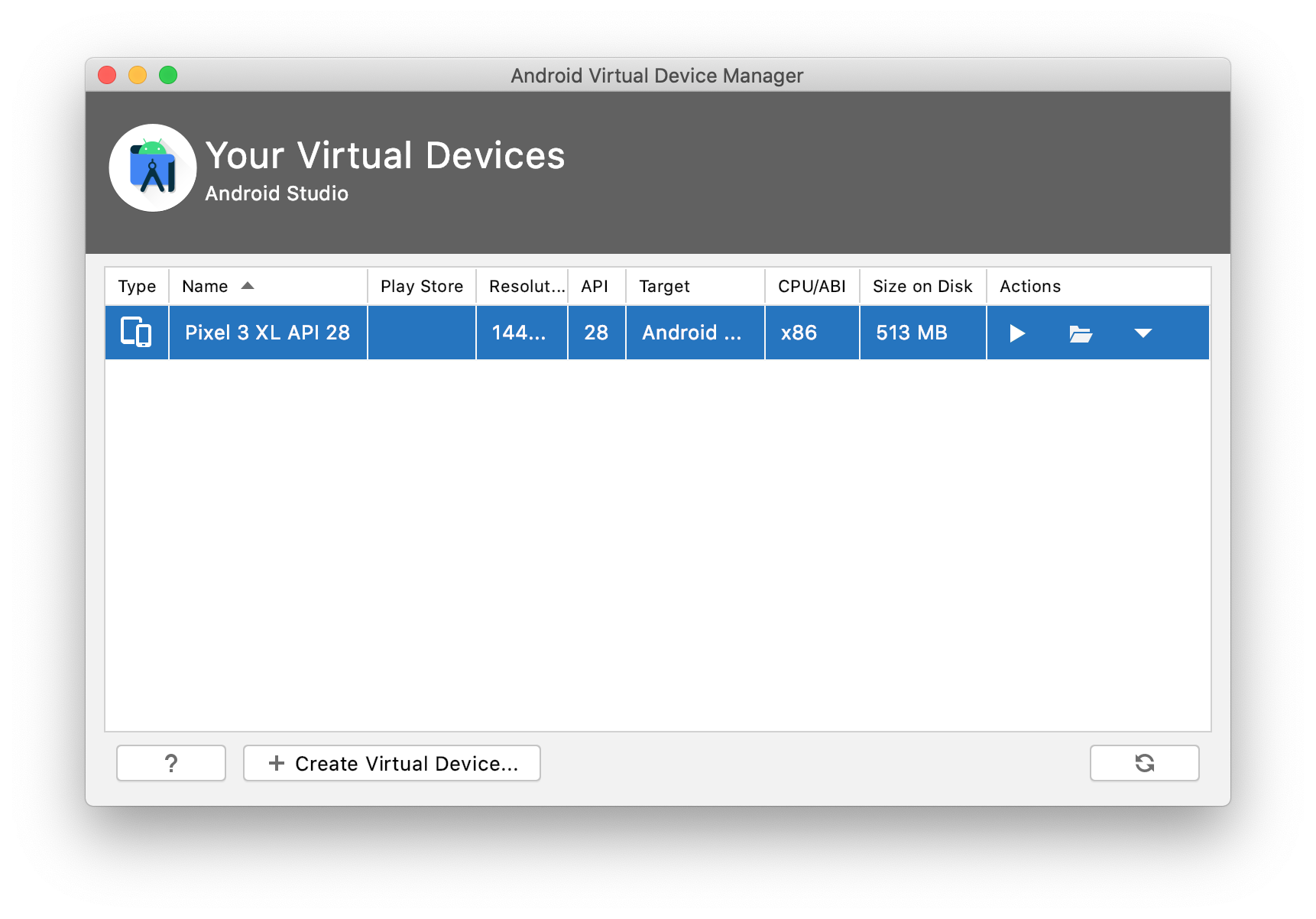
- Don’t launch the AVD from the AVD Manager yet.
Downloading the Google Play Services framework to side load
- Go to https://opengapps.org/
- Select x86 as platform, 7.0 for Android version and pico for the variant
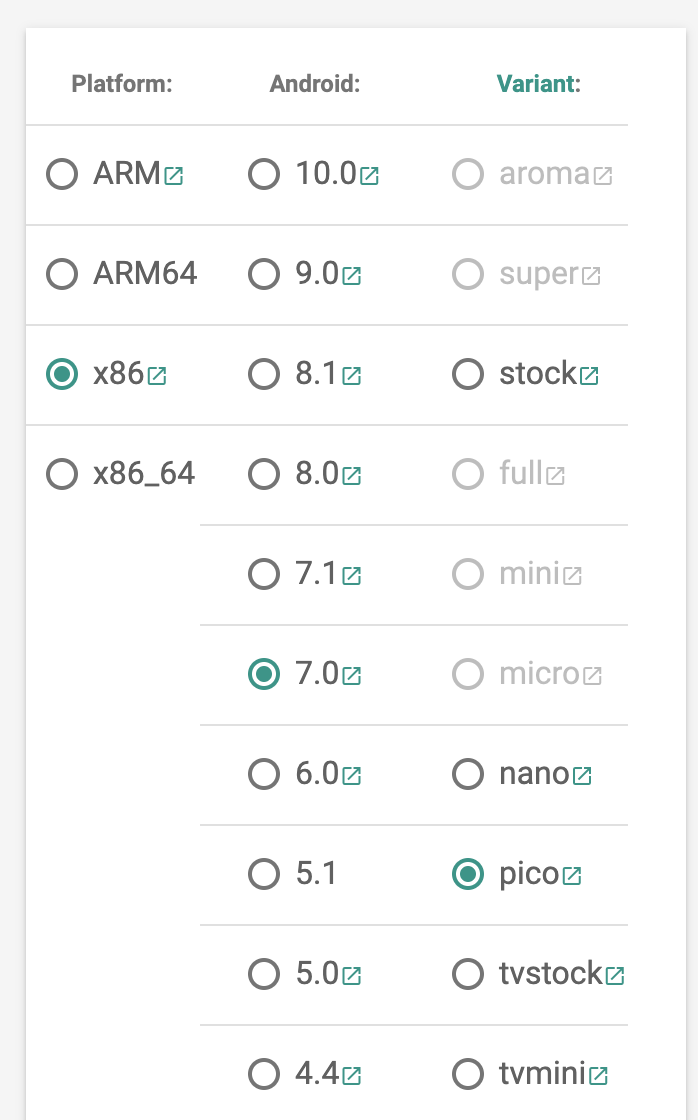
- Download and extract the zip file.
- There will be a bunch of zip files, you’re looking for the Phonesky.apk and GoogleLoginService.apk files
Preparing the AVD
- Open up your terminal
- Assuming you have your platform tools exposed in your $PATH you can type this to see what emulators are available on your system (including the one you just created):
emulator -list-avds - By default (when launched from the AVD Manager) we won’t be able to write any files to the system folders. To launch the emulator with writable system folders use this command:
emulator -avd Pixel_3_XL_API_28 -writable-system
Adding in the modifications for Google Play services
Open up a new tab in your terminal
adb root
adb remount
adb push Phonesky.apk /system/priv-app/
adb push GoogleLoginService.apk /system/priv-app/
Adding in the modifications for MITMproxy
-
cd ~/.mitmproxy/ -
adb shell "mount -o rw,remount /" - replace
c8750f0d.0in the following commands with what’s available in your folder. Additional details can be found here: https://docs.mitmproxy.org/stable/howto-install-system-trusted-ca-android/adb push c8750f0d.0 /system/etc/security/cacerts -
adb shell "chmod 664 /system/etc/security/cacerts/c8750f0d.0"
Reboot the emulator
adb reboot
Launching MITMproxy
- In your terminal run:
mitmweb - It should open your default browser and will be listening on port 8080
Setup the Proxy on the emulator
- Go to your network settings on the emulator
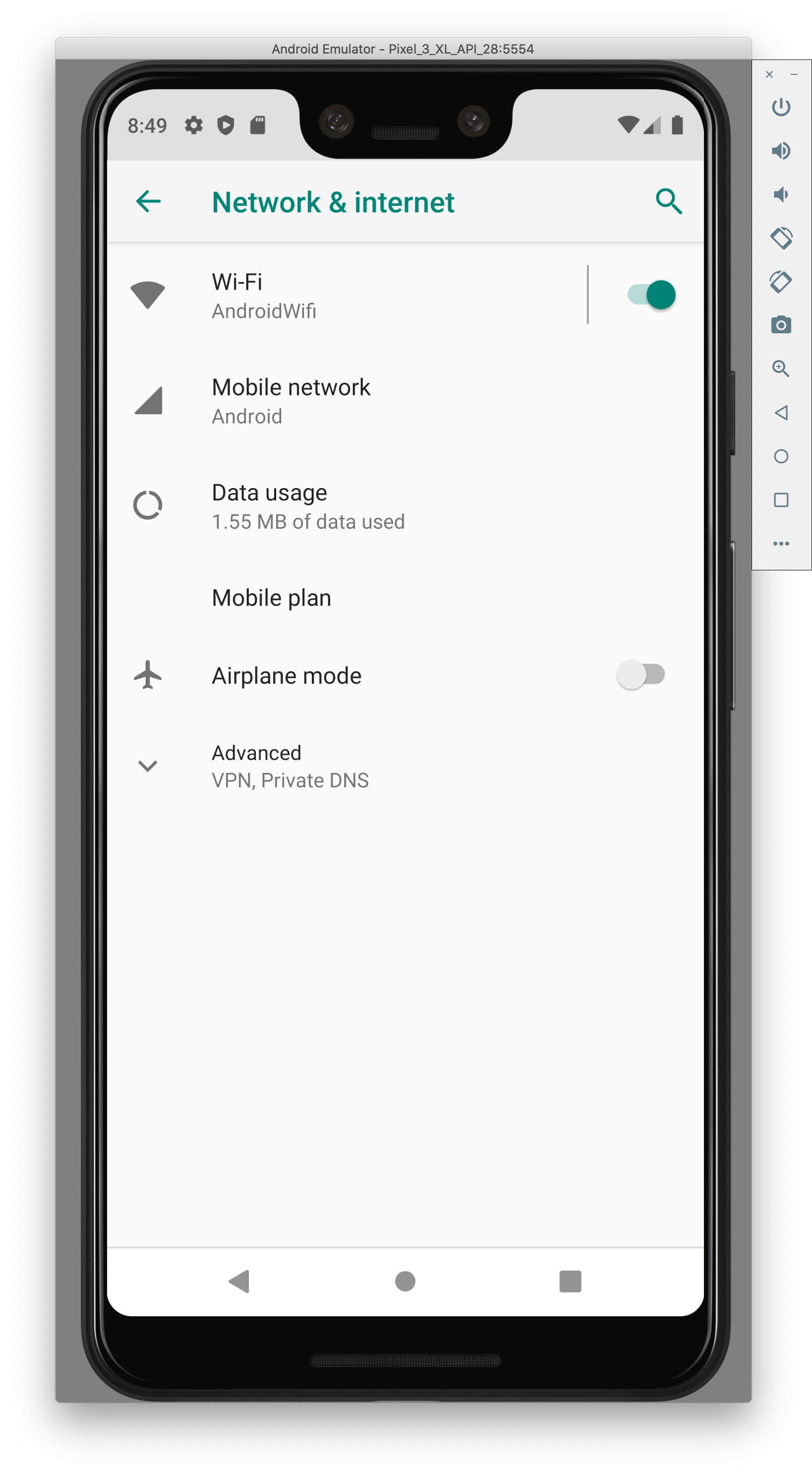
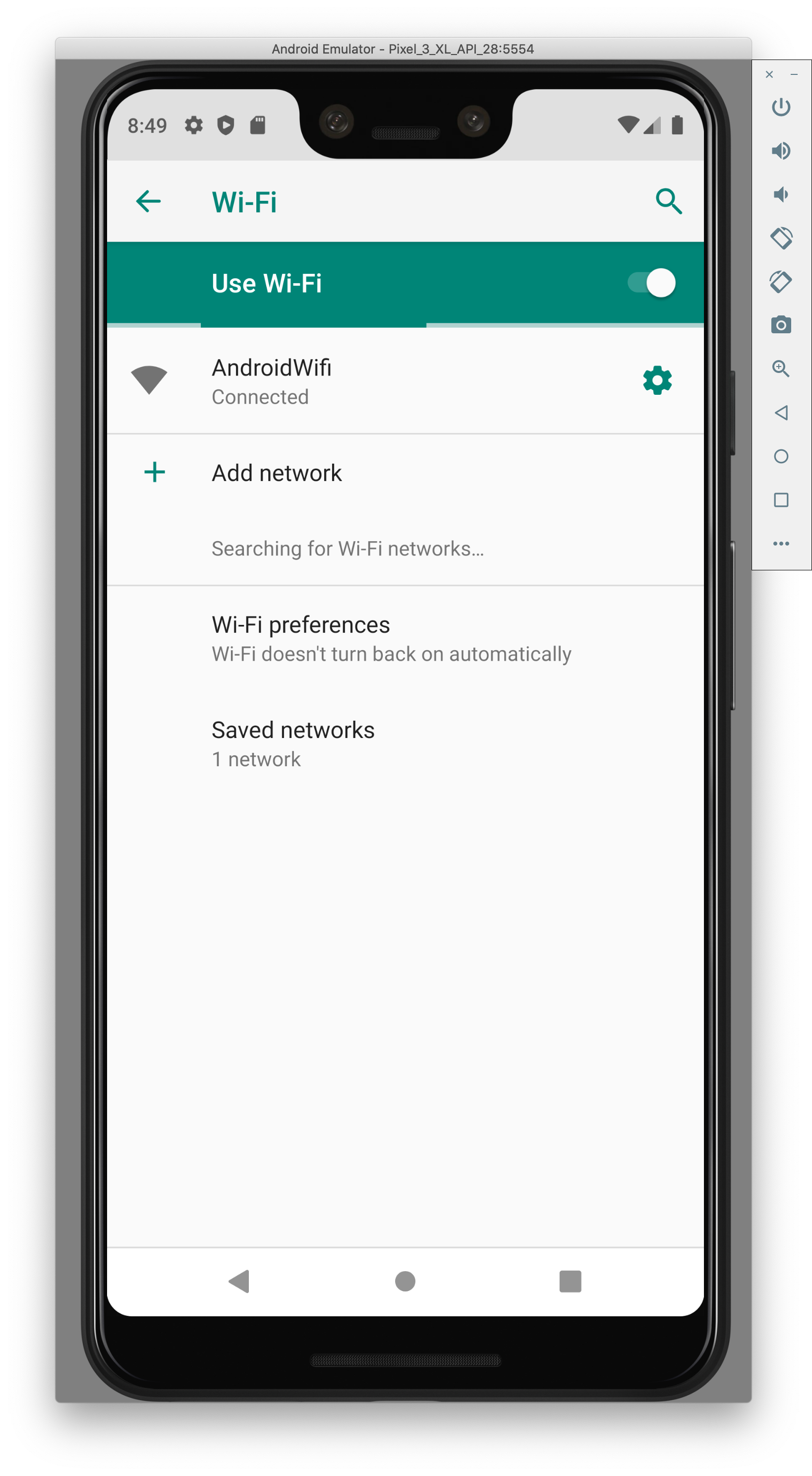
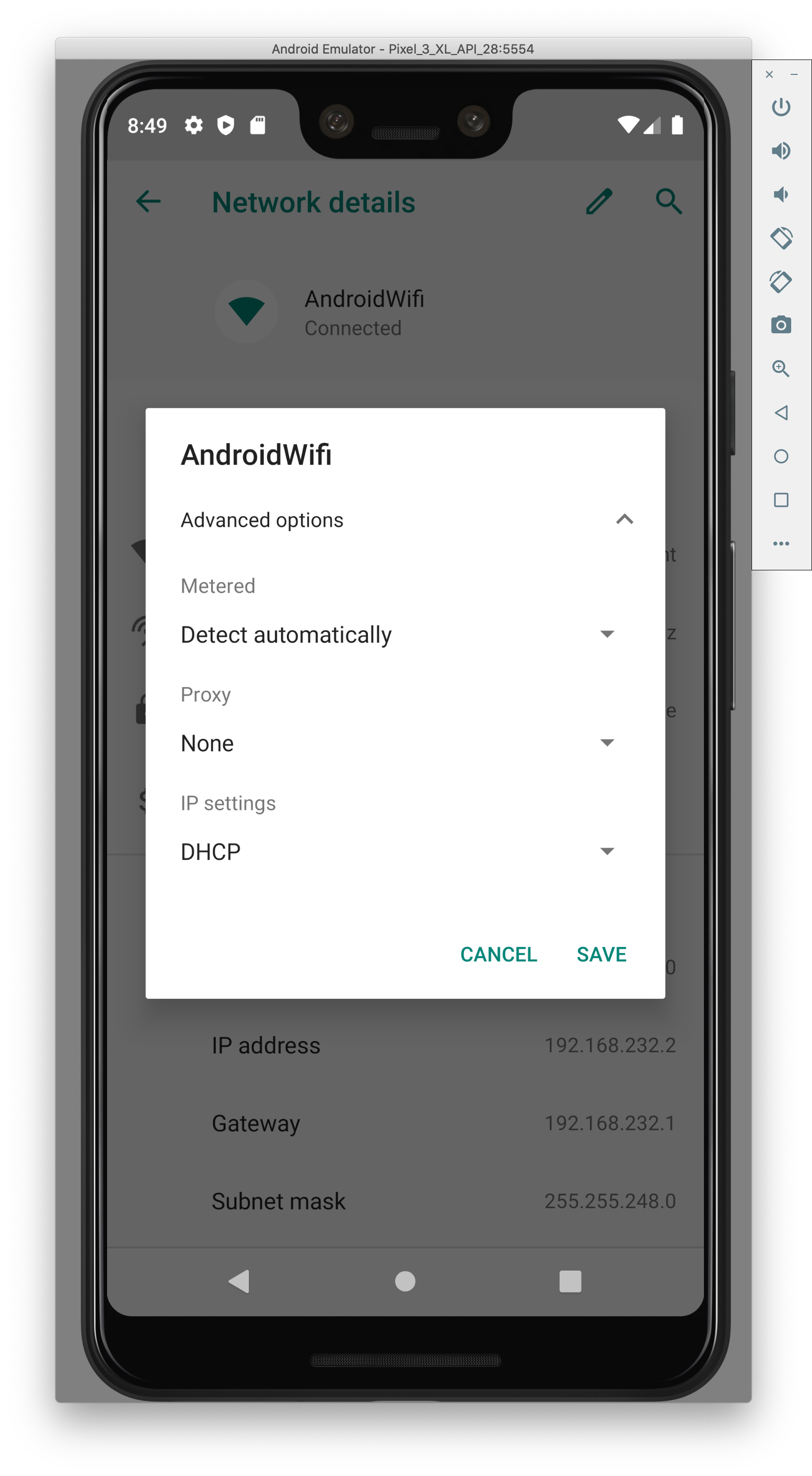
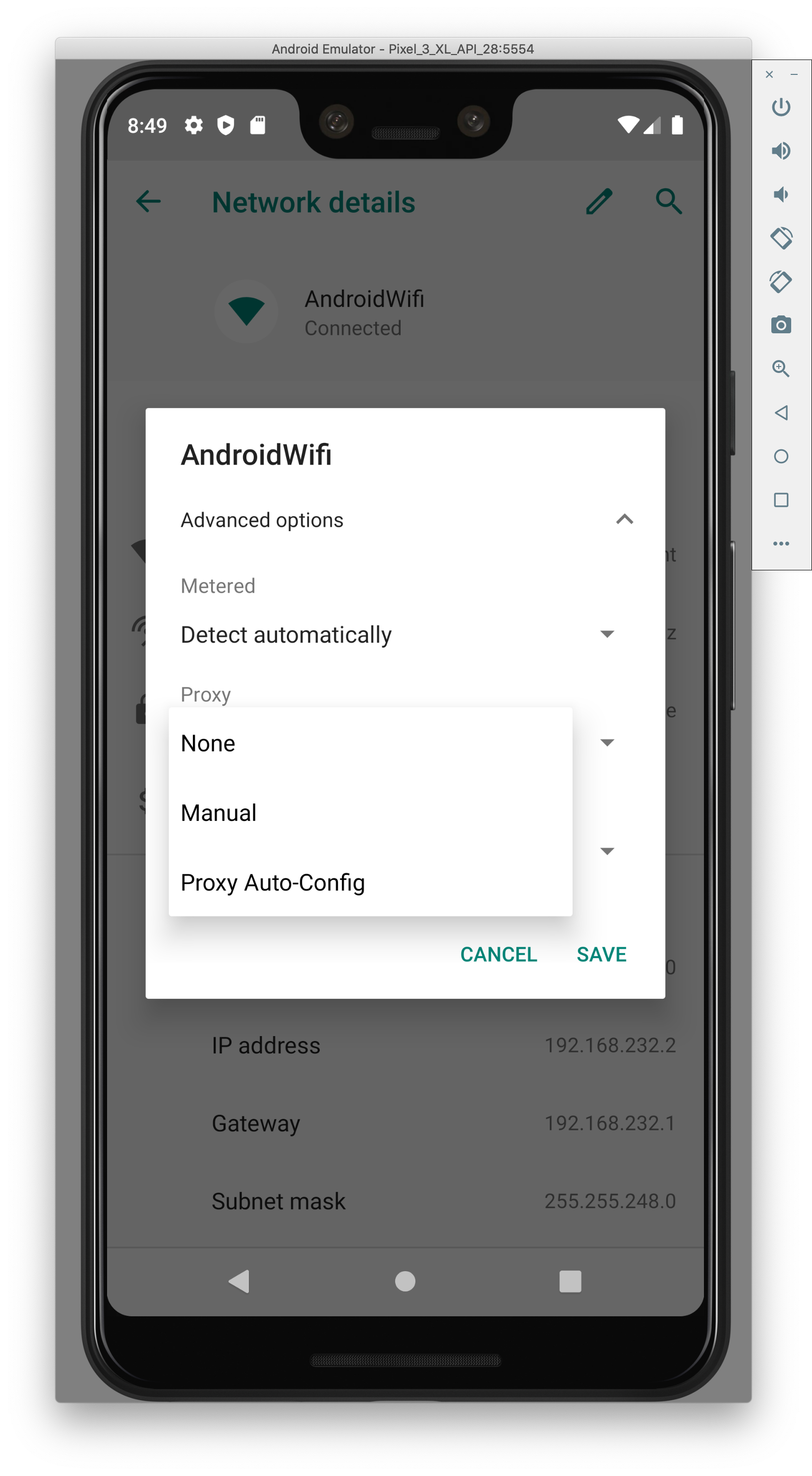
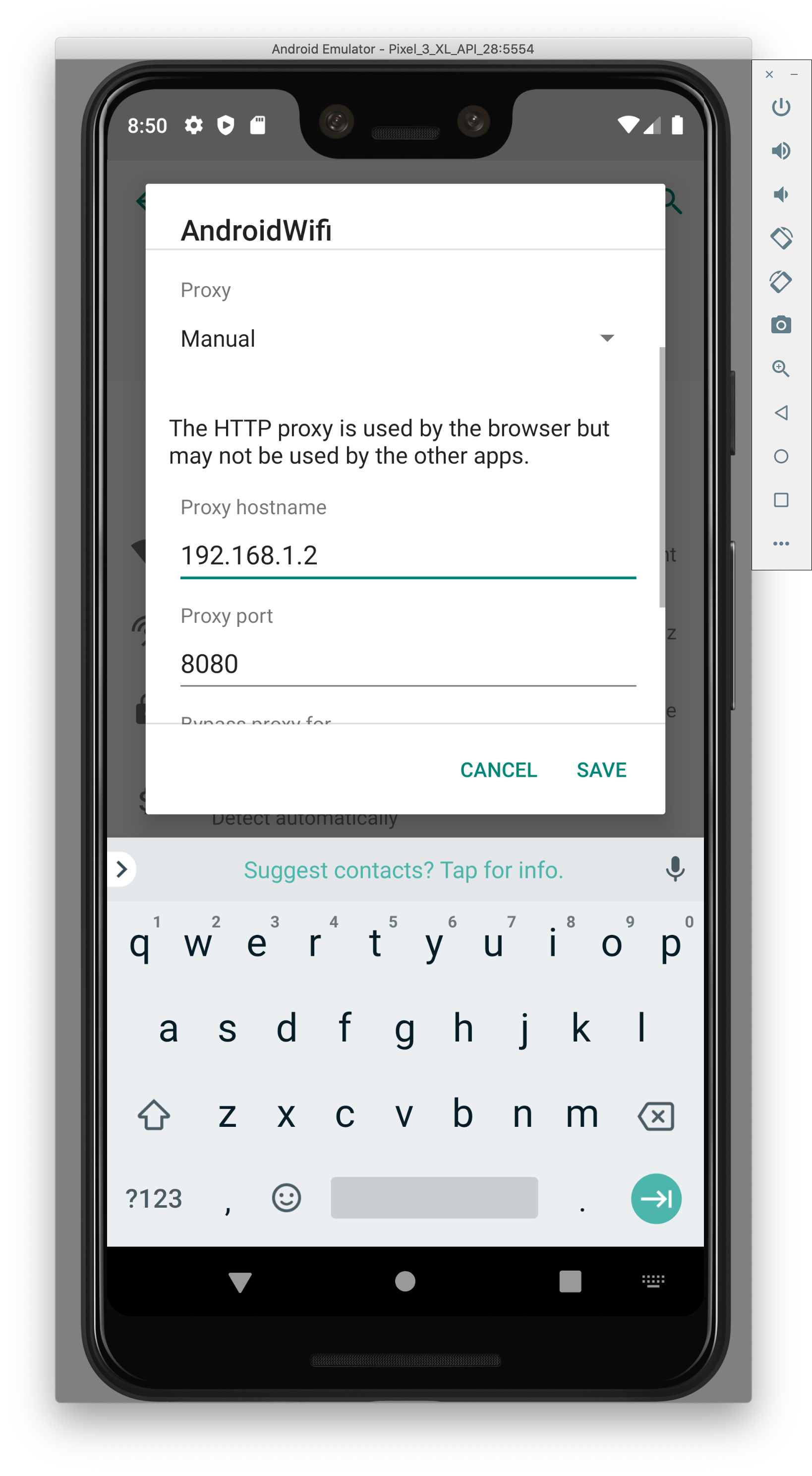
- Add in your local IP (use ifconfig to find it) and port 8080
- Open up the browser on the emulator and check the result of the page mitm.it
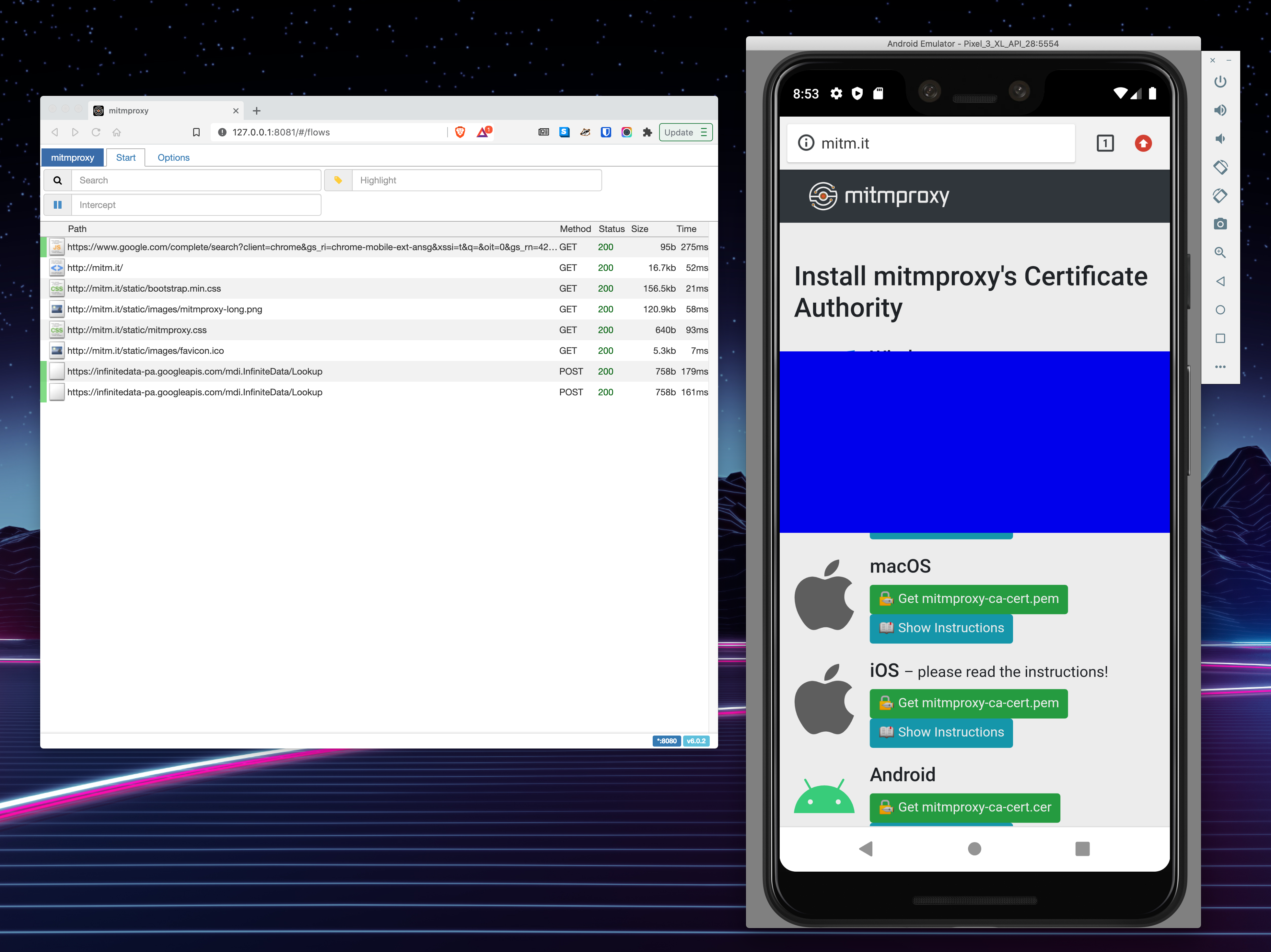
- You should start seeing messages in your MITMweb tab.
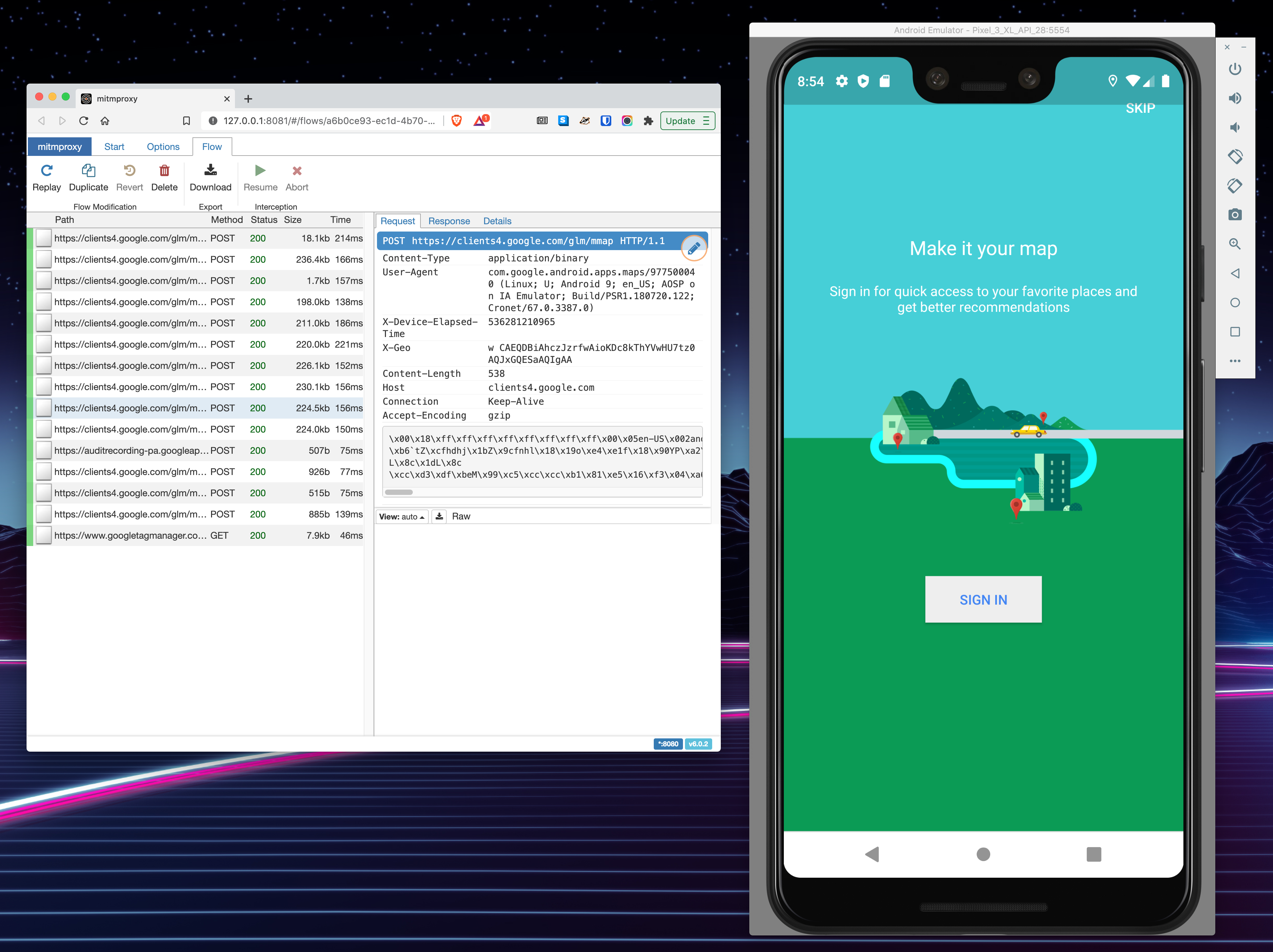
Now you should be ready to inspect some network traffic!
3 responses
Hi Laurence, great post. I followed all of the steps and was able to inspect network traffic through the browser but when I installed an app, for example kijiji it told me right away that the app needs google play services which is not supported on my device. I made sure to push the Phonesky.apk and GoogleLoginService.apk to /system/priv-app/ and after getting the error i double checked to make sure they were in priv-app. I am not sure what else I would need to do to get the app to run. Any ideas? Thanks
Hi, I’m stuck on the step of finding the .apk files from the openGApps release, ie > Download and extract the zip file. > There will be a bunch of zip files, you’re looking for the Phonesky.apk and GoogleLoginService.apk files When I download the pico release and unzip it, searching around I see a bunch of .lz files but none matching the name. I tried running installer.sh but it throws a warning to “Don’t run this on your computer, you need to flash the Open GApps zip on an Android Recovery”. My next move is to start manually untar’ing the various files, am I on the right track here? If you know which ones have the missing files can you let me know? Thanks
Jumped the gun, you just need a linux terminal with lzip installed, then you will find them like so:
tar -xvf /Core/vending-x86.tar.lzfor Phonesky.apk andtar -xvf /Core/gsflogin-all.tar.lzfor GoogleLoginService.apk